Forensic investigation using Open-Source Intelligence (OSINT)
- Cybersecurity
A criminal record may be scattered across networks with several different identities, thus forensic analysis of evidence on acquired devices is no longer the most reliable method.
Gathering information about a culprit’s identity from publicly available sources is an important factor and a vital piece of evidence. To ease the amount of labor and provide the required services promptly, various tools are now available for the investigator. There are free as well as commercial tools available. Open-source tools can be considered an important weapon for the investigator. It broadens the scope for an investigator to gather publicly available information about the target, relate the gathered information, validate, and perform further investigation.
Various methods based on specific cases can be used for gathering information such as:
1. Yandex, Tineye, Google image search, etc. can be used for a reverse image search. These are useful tools to identify whether the target is using images from online sources.

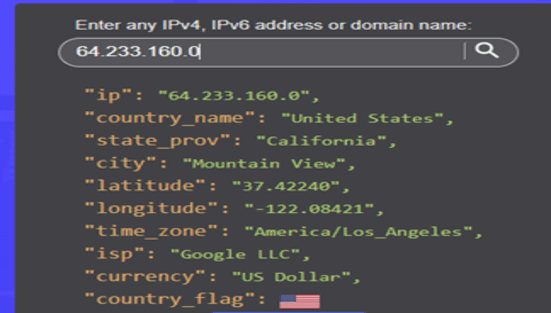
2. IP geolocation: To identify the location of the culprit with useful metadata. The below images show the details of one of the google IP locations and its metadata.
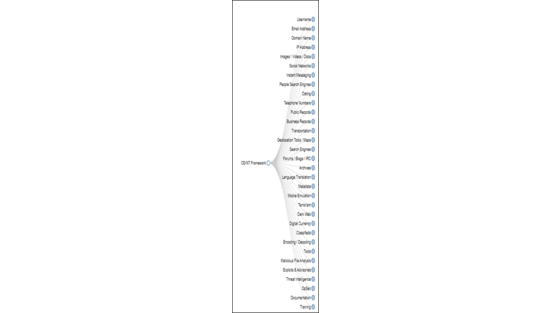
3. OSINT framework: A vast collection of open-source tools for gathering information about the target include search for username, email, domain, IP address, phone number, malware analysis, dark web, terrorism, etc.
4. Social media analysis like who tweeted first to identify the creator of tweets, hashtag tweet to identify the individual or organization supporting terrorism, spreading false news through any social media platforms.
Opensource eliminates the requirement for checking individual platforms, as using a single tool can traverse across networks and check for possible existence of information such as images, name, phone number, email, etc.
Example: A crime was committed through phone number XX, and the task is to find who uses it and where? In such a scenario, True caller, Phoneinfoga, or other phone information identifier tools can be used. As it is possible, XX may be used in many platforms. Now, if additional information is obtained say ‘n’ usernames, then username finder tools can be used for further investigation and so forth.
As the crime rate is rising exponentially, it is important to resolve the issue at the right time before harm is done. Thus, Opensource tools being free to use by anyone have shown a promising outcome for any investigator.
With the right tools and approach, proper measures can be taken by investigators or law enforcement before it brings chaos or disharmony to society.
About the FutureSkills Prime Programme:
FutureSkills Prime, a collaborative effort by nasscom and MeitY, serves as India's technology skilling hub with the objective of transforming the nation into a Digital Talent Nation. The program facilitates widespread access to learning, empowering both students and professionals to enhance their digital expertise and professional competencies. The comprehensive range of courses available through FutureSkills Prime encompasses a diverse array of digital technologies and vital professional skills.
<
Written by NIELIT Kohima


